What is a Risk Matrix?
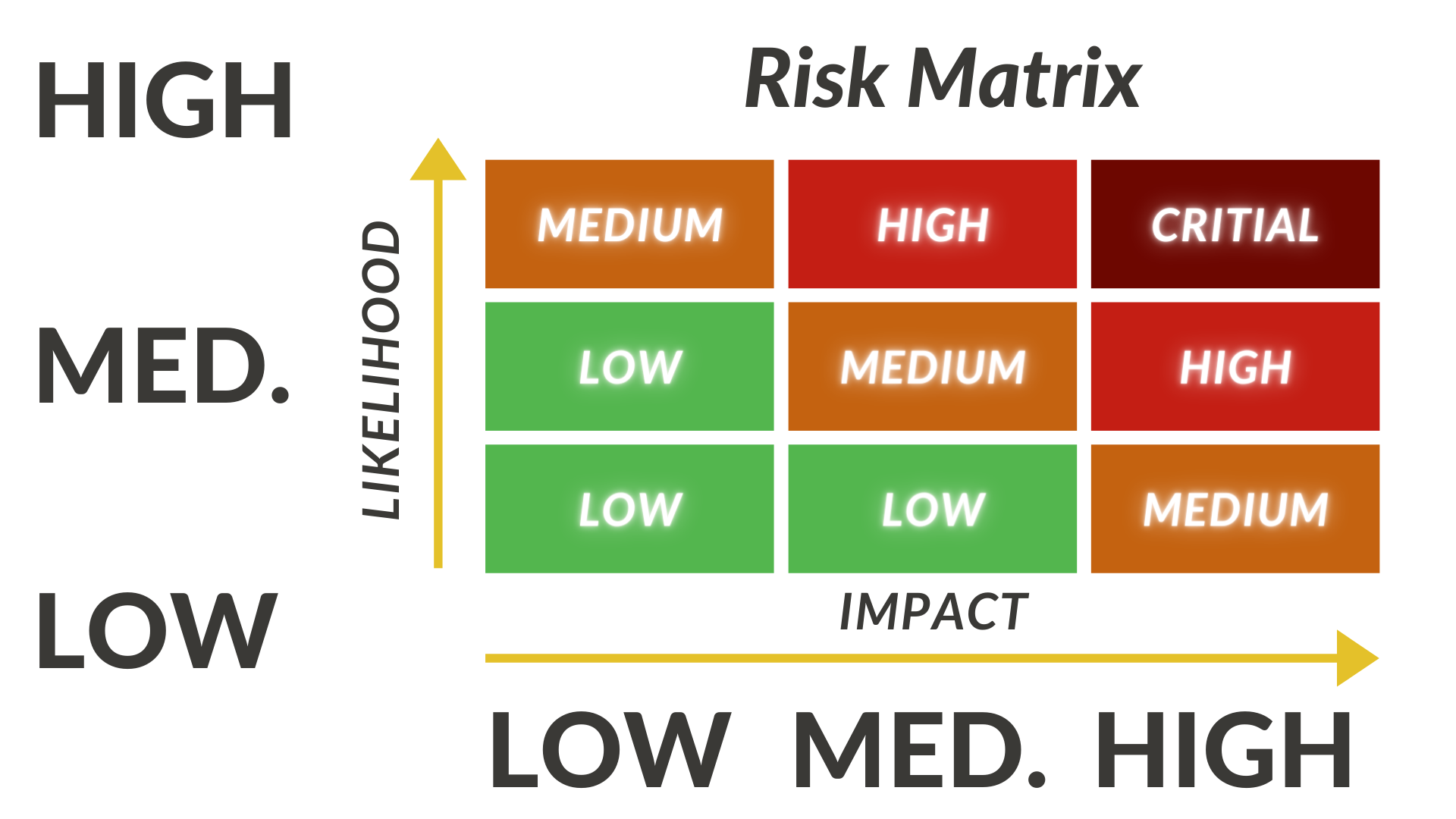
A risk matrix is a risk assessment tool that is used to visualize the likelihood of a risk occurring. You can think of a risk matrix like the upper right quadrant of a cartesian graph. The x-axis of a risk matrix denotes the likelihood of an occurrence taking place, and the y-axis would denote the extent of the damage that risk occurrence would create. By this model, an observer can get a qualitative understanding of the likelihood of the occurrence taking place by assessing where an occurrence falls on the risk matrix. Often, risk matrices will use color coding to visually represent the likelihood of different risks.
For example, an occurrence found in the bottom left portion of the risk matrix will express an event with a low likelihood of occurrence and a low impact on the business if it occurs. The event in this example may be colored green to visually represent a low risk. In comparison, an occurrence in the upper right-hand quadrant of the risk matrix would have a high likelihood of occurrence and have a high impact on the organization if that event occurs. The event in this section of the risk matrix may be colored red to denote a high-risk severity and a high priority to address mitigating the occurrence of this event. The risk matrix provides organizations with a
Risk Assessment Matrix
A risk assessment matrix is a quantitative risk assessment strategy that not only identifies the likelihood and the estimated damage of an occurrence but also looks to quantify their outcomes based on probability. The risk assessment matrix is designed to populate the risk matrix with probabilities so that any given occurrence should have an estimated probability of that event occurring. An organization would create a risk assessment matrix by assigning probabilities along the x and y-axis of the risk matrix. For example, the x-axis may start at .1 and increase to .8, and the same holds for the y-axis.
By applying some simple matrix math and multiplying the x-axis value by the y-axis value at a specific point (exactly like using a cartesian graph), it will render a matrix of probabilities on the risk assessment matrix. Now, an organization can assess the risk likelihood in how one event may compare to another with a high level of granularity. The higher the number, the higher the potential risk associated with that event.
Once an organization has gathered each event’s associated probabilities, they can order the events in ascending order from very high probability to very low probability to help make more informed decisions related to risk mitigation.
Risk Management
Cybersecurity Risk Management is the process of identifying, evaluating, and strategically minimizing an organization’s risk. It’s important to note that risk can come from many different aspects of an organization. Whether it’s the risk of a data breach or a faulty product incurring a recall, the risk doesn’t affect one sector or a single organizational unit. For this reason, it’s critical for risk management teams to assess the level of risk across all organizational units and facets of an organization.
To this point, risk management often depends on risk assessment matrices that aim to survey any and all business units, often requiring stakeholders from various segments of a business to provide insight into what risks their specific business unit may face.
Matrix Assessment Template
For organizations that are interested in assessing their internal risk, a great place to start is to form a risk assessment committee or a risk project management team and leverage the resources that are immediately available. Today, there are countless risk assessment templates available online. Often found as free excel templates, you can quickly start identifying, evaluating, and managing risk. This can be a great first step to building an internal risk evaluation. However, building a formal risk assessment team based on the input of risk experts may be a good long-term initiative to mitigate the various risk occurrences.
